|
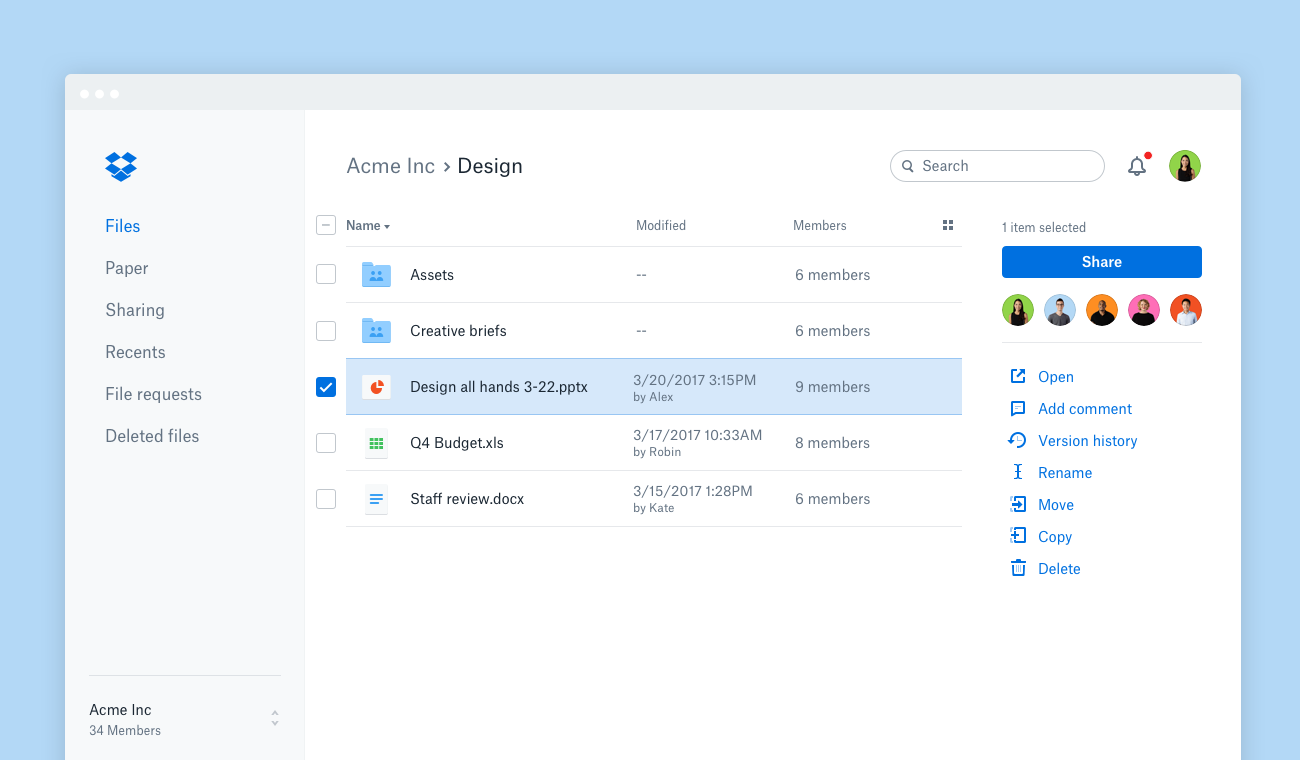
In addition to providing business technology guidance to companies, I’m often asked which personal technologies are the best. As we wrap up 2017, I'm sharing my best of 2017 recommendations in this series of articles. For this best of 2017 review, I will cover the most requested personal technologies in a series of weekly articles. This week’s article will cover the best: 5. To-do list App 6. Printer (personal/small business) 7. Home Security Cameras 8. Data storage (Cloud service, personal NAS… the best way to store your data) The Best To-Do-List App: TodoistStart your new year getting better organized with the best to-do-list app, Todoist (www.todoist.com). This category recommendation changed from last year. For many years the best to-do-list app was Wunderlist. But unfortunately, Microsoft purchased Wunderlist, and frankly, they ruined it. This year Microsoft announced that they are ending support for Wunderlist, and attempted to move the Wunderlist functionality into their own new Microsoft To-Do app. So far, those plans are a failure. Microsoft To-Do lacks some key features that were in Wunderlist, and Todoist has added new features, which makes Todoist the new top pick for a to-do-list app. I have tried many different to-do-list apps, and while each can provide a basic list, the easy of use, intuitive user interface, ability to reliably sync your to-do-list between all your devices, and integrations with other apps (such as Amazon Echo/Alexa) sets Todoist apart from the others. The base version of Todoist is FREE, and even the base version will satisfy most user's to-do-list needs. The Best Printer: Epson WF-4720Printers come in many varieties, and the best option depends on your particular needs. For an individual or a small business, I recommend an all-in-one color printer with an automatic document feeder. For a negligible price difference versus a printer-only device, the all-in-one also provides you a scanner, a copy machine and a fax. The best all-in-one printer is the Epson WF-4720. This one device provides a great color scanner with a high-capacity document feeder, a color copier, a color printer, and a fax, and it's the fastest printer we have ever tested. Typically ink jet printers are very slow, but Epson upgraded this model with their new print technology, and it is shockingly FAST. Who wants to wait on your pages to print?.... nobody. So, when you buy a printer, purchase one that has the right functionality, great print quality AND great print speed. The Best Home Security Camera: Nest CamMany people are looking to upgrade their home security. The home security market has greatly expanded this year, and the market is now flooded with options. One consideration is whether you want just security cameras, or do you want a full home automation system that controls your lights, door locks, thermostat, appliances, and other home functions. In either case, the Nest products are a great place to start. The Nest Cam is very easy to setup, has very solid build-quality, and the video quality is excellent. The Nest app is excellent, and provides a hub to manage all your Nest products. Nest also integrates well with other popular home automation products and hubs, such as Amazon Echo/Alexa and Nexia. Nest offers the ability to capture the video in the Nest Cloud, which provides you convenient way to access your camera videos from anywhere, and the security of having a copy of the videos at a secure, offsite location....if a thief steals your valuables and your cameras, you will still have a copy of the videos to provide to the police. The Nest Cam can also be configured to send an alert to your phone whenever a person is detected in a designated area (such as your front door or back door), which is another great security feature. And once you receive the alert, the Nest App allows you to have two-way conversation with the person through the microphone and speaker that is built into the Nest Cam. Overall great features and the Nest ecosystem make the Nest Cam the best. The Best Data Storage: DropboxOne of the most frequently asked technology question is "What is the best way to store all my files/data"? Over the years, cloud data storage options have changed the way we store and share our files. One of the first providers of cloud data storage was Dropbox, and now even many years later, they are still the best. This recommendation is for individual use, not a large business/enterprise. The needs are different for a large business/enterprise, and that recommendation will be covered in another article. Today, there are many options for storing your data, with an ever-growing list of cloud data storage providers and new "private-cloud"/NAS options. Let's review the cloud storage options. Google Drive continues to improve and offer new interesting features. Microsoft OneDrive is becoming more compelling with their bundling of 1TB of OneDrive storage with an Office365 plan. I have used all of them extensively, and frequently compare notes with my fellow technology professionals, and the one that everyone keeps coming back to is Dropbox. It's convenient, reliable, and has the best user-interface. Private Cloud/NAS: Some people ask about setting up their own "private cloud", by purchasing and configuring a NAS (Network Attached Storage). While the privacy of your own NAS may sound compelling, when you consider the cost and hassles, your private cloud typically isn't worth it. We recently setup our own NAS for an evaluation. We spent thousands of dollars to purchase all the components, many hours configuring it, and it will continue to require maintenance. For the total cost of this NAS, we could have purchased 10+ years of a Dropbox subscription. And the NAS will most likely require even more costly hardware replacements within the next 5 years (or sooner). With your own NAS, you will still need an offsite, backup copy of your data, which will is another additional cost. Overall the cost comparison and hassles of having your own private cloud hardware just doesn't make sense. Please note: I recommend that you do NOT keep confidential and/or sensitive data in any Cloud service. Instead, keep confidential and highly sensitive data on your own, private encrypted drive and back it up frequently with another, encrypted USB drive(s). Once the backup is complete, keep the backup drive disconnected from your PC and in a separate, secure location. A case can be made for each of the options, but overall I recommend Dropbox for your primary data storage. With pricing continuing to change and new features being added, this recommendation may eventually change. We will continue to test all of them and monitor the progress, so stay tuned. To see the other best of 2017 technologies (categories 1-4), click here.
0 Comments
In addition to providing business technology guidance to companies, I’m often asked which personal technologies are the best. As we wrap up 2017, I'm sharing my best of 2017 recommendations in this series of articles. While many technology magazines provide their recommendations for the best technology, their opinions are typically formed in their lab and can be biased based on their advertisers and alliances. The Advantages: My recommendations are not influenced by advertising, corporate sponsors or other relationships that can impact magazine recommendations .... I simple recommend the best technology. My recommendations are based on a much larger testing environment that includes extensive hands-on experience, feedback from a very wide variety of customers and environments, 30+ years as a technology leader and global technology advisor, and leveraging feedback from a large resource pool of other global technology experts and their experiences. For this best of 2017 review, I will cover the most requested personal technologies in a series of weekly articles. This week’s article will cover the best:
The Best Smartphone: Apple iPhone XOver the years I have used both Android and Apple phones. I used an iPhone for many years, and three years ago I switched over to Android. Until recently, my primary phone was an Android phone, the Samsung S7 Edge. Experts point out that the both Android and Apple have the strengths, and I agree. Like many technology professionals I have historically tried to avoid being on the Apple bandwagon, and liked the flexibility of Android. I reviewed the latest offerings, including the Samsung Note 8, the Samsung Galaxy 8, LG V30, Google Pixel 2, and many others. But, the iPhone X just look Apple to another level, and after using the iPhone X for several months, it is without a doubt the best phone I have ever used. The form-factor of the iPhone X feels really nice in your hand, and is well-balanced. The Note 8, iPhone 8 and other smartphones with comparable screens feel top-heavy and awkward in your hand, and lack the “just-right” feel of the iPhone X. The iPhone X’s Face ID works great, there is never a screen lag (like you see on Android phones), it has amazing battery life, and the best overall user experience. Sorry Android fans, Apple created a winner, and overall the iPhone X is the best. The Best Smartwatch: Apple Watch Series 3I have used many different smartwatches, including Android Wear, Samsung Gear, FitBit and Apple. For the past two years my preference has been the Samsung Gear S3 Classic Watch. The Samsung Gear looks great, but the battery life was terrible (it often couldn’t last a full day) and the lack of apps was very disappointing. By far, Apple has the best selection of apps for a smartwatch, and with the Apple Watch Series 3, they finally got the hardware right. With the Apple Series 3, I typically have more than 80% battery life available at the end of the day, and I’ve gone 3 days on a single charge. The Series 3 also adds the cellular capability and phone number mirroring with your iPhone, which gives you the ability to leave you phone at home and still send/receive your calls and messages. The apps, the user interface, the heart rate monitoring, and the overall experience is better on the Apple Watch. Smartwatches will continue to evolve, but currently the Apple Series 3 is the best smartwatch. The Best Laptop: Dell XPS 13The form factor, The Dell XPS 13 fits a 13” screen in a 11” form factor. The amazing display is a stunning, edge-to-edge (nearly borderless, infinity display. The size, weight, case material, aesthetics, included ports, and performance are all superior and all make the Dell XPS 13 the best overall laptop. For those that want a 15.6” display and even more horsepower (most people don’t really need it), my recommendation is the larger Dell XPS 15. HP has made improvements, but their awkward trackpad, and overall configuration can’t match the Dell XPS. Lenovo, Samsung and others have too many quirks and quality issues to be a contender. Apple has their following, but the current line of Apple laptops are disappointing, and their core components and overall value can’t match the Dell XPS. The Best Home Technology: |
AuthorMark Johnson is the Chief Executive Officer at Xtrii. He is a 10x CIO, global technology advisor and business leader. He has received global awards and recognition for excellence in technology and innovation. Archives
April 2020
Categories
All
|
















 RSS Feed
RSS Feed